Top 25 Splunk Interview Questions and Answers
1.What is mean by Splunk?
Splunk capture, index, & correlate the real-time data in the searchable repository. This is from the repository data, it generates the graph, report, alert, dashboard, and visualization. It allows us to get visibility into the machine data. It is generated from hardware devices, network servers, IoT devices and other sources. Splunk is used for analyzing machine data.
2.What are all different areas, Splunk can be used?
Splunk enables access to machine data across the organization. This is achieved via identifying the data patterns from repository. Also, it provides metrics, diagnosing problems and providing solutions for business operations.
3.List the components used in Splunk architecture?
Following are some of the components used in Splunk architecture,
- Search Head – It Provides the GUI for search.
- Indexer – It Indexes the machine data.
- Forwarders – It Forwards the logs to indexers.
- Deployment Servers – Manges the Splunk component in the distributed environments.
4.State the difference between Splunk and Spark?
| Conditions | Splunk | Spark |
| Positioning Area | Machine generated data is collected in large amount | Processing interactive applications as well as in-memory process |
| Nature of the tool | Proprietary | Open sourced |
| Mode of work | Streaming modes | Both streaming and batch mode |
5. Give some of the common port numbers used in Splunk?
| SERVICE | PORT NUMBER USED |
| Splunk Web Port | 8000 |
| Splunk Management Port | 8089 |
| Splunk Indexing Port | 9997 |
| Splunk Index Replication Port | 8080 |
| Splunk Network Pork | 514 (used to get data in from network port i.e. UDP data) |
| KV Stores | 8191 |
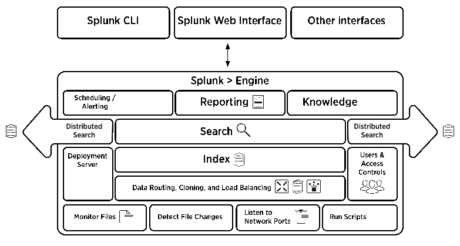
6. Can you draw the Architecture of Splunk?
The following image gives the brief Architectural view of Splunk
There are 3 main components in Splunk:
- Splunk Forwarder, used for data forwarding
- Splunk Indexer, used for Parsing and Indexing the data
- Search Head, is a GUI used for searching, analyzing and reporting
7. What is mean by Splunk forwarder and types of Splunk forwarder?
It is a free and dedicated version of Splunk Enterprises. It contains only the essential components which are needed to forward data. It is used by TechSelect to gather data from a variety of inputs and forward machine data to Splunk indexes. The data is then selected for searching.
There are two types of Splunk Forwarder. They are as follows,
- Universal forwarder (UF): Splunk agent is installed on the non-Splunk system. It is used to gather data locally. It can’t parse or index data.
- Heavy weight forwarder (HWF): It is full instance of Splunk with an advanced functionality. It works as a remote collector, intermediate forwarder as well as possible data filter. They parse data. It is not recommended for the production systems.
8. Explain Splunk indexer? List the stages of Splunk indexing?
The Splunk enterprises component that is used to create and manage the indexes is known as Indexer. The primary functions of an indexer are
- Indexing incoming data.
- Searching the indexed data.
9. What are the uses of License Master in Splunk?
It is responsible for conforming that the right amount of data gets indexed. Splunk license is based on the data volume that receives to the platform in 24 hrs. It plays a major role in conforming that the environment stays within the limits.
10. What will happen when the License Master is unreachable?
We can’t able to search the data when the license master is unreachable. The data coming in to the indexer will not be affected. The data will come to Splunk deployment continuously. The indexers will continue to the index as usual, but we will receive a warning message on the top as exceeded the indexing volume and reduce the amount of receiving data or you need to purchase the higher capacity license.
11. What is mean by License violation?
License violation error occurs when the data limits exceeded. The license warning is popup and it will stay for 14 days. While we use commercial license, we will receive warning 5 times in 30 days rolling window before our index search result and report stop triggering. While we use free version, we will receive waring for 3 times.
12. List the types of Splunk Licenses?
Following are some of the Splunk Licenses,
- Enterprise license.
- Free license.
- Forwarder license.
- Beta license.
- Licenses for search head (used for distributed search).
- Licenses for cluster members (used for index replication).
Related Courses
AppDynamics Training in Chennai
PRIVATE 4259Cyber Security Training in Chennai
PRIVATE 578Devops Training in Chennai
PRIVATE 213. List some of the features that is lagging in Splunkfree?
Following are some of the features that is lagging in Splunkfree,
- Authentication as well as scheduled searches or alerting.
- Distributed search.
- Forwarding in TCP as well as HTTP to non-Splunk.
- Deployment management.
14. Brief about Search Factor (SF) and Replication Factor (RF)?
The Search Factor controls the number of searchable copies of indexer cluster-maintained data. The default value of search factor is 2. The replication factor in the case of indexer is minimum number of copies of each search artifact. The Search head cluster has search factor only. Index cluster has both search factor as well as the replication factor. The search factor should be less than or equal to the replication factor.
15. What is use of Time Zone property in Splunk and when it is required?
Time zone is very important when we search for the events from a security or fraud perspective. If we search with wrong time zone we will end up and unable to find the event. It will pick up the default time zone from the setting of the browser. It usually picks up the current time zone from the system we are using. It usually picks up time zone when data is input when we search as well as correlating data coming from different sources.
16. Explain Splunk app? How it differs from Add-on?
Splunk App is said to be entire collections of reports, dashboard, alerts, field extractions and lookups. Splunk Add-on means the visual component of a report or dashboard minus Splunk Apps.
17. Give few examples of regular expression for extracting IP address from logs?
There are many ways to extract Ip address from logs. Following are few of them
Regular expression for extracting IP address:
rex field=_raw “(?<ip_address>\d+\.\d+\.\d+\.\d+)”
Or
rex field=_raw “(?<ip_address>([0-9]{1,3}[\.]{3}[0-9]{1,3})”
18. Explain briefly about troubleshoot Splunk performances issues?
We should check the splunkd.log for the any other errors. We should also check the server’s performance issues. We must install the SOS app & check for the warning as well as errors in dashboards. Also, we should check for the numbers of the saved searches which are currently running along with the systems resource’s consumptions.
We should install the firebugs which is the extension of firewall. After it is installed & enabled the log into the Splunk, an open firebug’s panels. After that switch to net panel. It will show HTTP requests along with time spend in every HTTP. It will provide us lot of info.
19. What do you mean by Buckets and explain its life cycle?
Splunk keeps index data in directories. It is known as Buckets. Simply it is a directory containing events of certain periods.
The bucket moves several stages they are as follows,
- Hot: It contains new indexed data which is open for writing. There may be one or more hot buckets for each index.
- Warm: It contains data which is roll from hot. There may be many warm Buckets.
- Cold: It contains data which is roll from warm. There may be many cold Buckets.
- Frozen: It contains data which is roll from Cold. The indexer deletes the frozen data by default, but we can archive it. Archived data can be later thawed.
20. What are Stats & eventstats command?
The Stats command are statistics of the all existing field in our search result as well as saved them as the values in the new field. Eventstats is same as stats command excepts the aggregation result is added to the event. Eventstats calculates the required stats but aggregate them to original data.
20. How do you exclude few events from indexed by Splunk?
We can achieve this by defining regex. It matches the necessary events and send it to null queue. Following is a simple example to do this,
<code>[source::/var/log/foo]
#Transforms must be applied in this order
#to make sure event are dropped on the
#floor prior to making their way to the
#index processor
TRANSFORMS-set=setnull,setparsing
</code>
In transforms.conf
[setnull] REGEX = .DEST_KEY = queue FORMAT nullQueue
[setparsing]
REGEX = login
DEST_KEY = queue
FORMAT = indexQueue
22. Explain search head pool & search head clusters?
Search head pool as well as Search head clusters are features. It provides Splunk for the highly available of the search head in the case any search heads go down. The Search head clusters is introduced newly. Pooling will remove in the next upcoming version. Captain is being managed by search head cluster. captain controls the slave. Search head clusters is reliable & efficient compared to pooling.
23. Explain dispatch directory?
$SPLUNK_HOME/var/run/splunk/dispatch will contain a directory for each search that is running. For Example, a directory which is named as 1434308943.358 contains a CSV file. This file will contain search result, a search.log with the details about the search execution and other details. These directories will be deleted after 10 mins after the search is completed. We must save the result since it will be deleted after 7 days.
24. What is mean by MapReduce algorithm?
The MapReduce algorithms is the secret behind the Splunk data searching the speed. Batch based on large scales parallelization uses this algorithm. It is based on the functional programming map() as well as reduce() functions.
25. How inputlookup and outputlookup are used in Splunk search?
The inputlookup command will return the search result as the whole table lookup.
For example
…| inputlookuplookuptabellename retuns the search result of each row in the table lookup with two field.
?values:
- host
- machine_type
The outputlookup command will return the output of the current search result of the lookup table on the disk.
For example
…| outputlookup lookup.csv saves all the result into lookup.csv.
26. Explain about Splunk SDK & Splunk Frameworks?
Splunk SDK is designed to develop the apps. The apps are developed from ground up. It doesn’t require the Splunk Web / any component from Splunk Apps frameworks. This will not alter Splunk software. It is a separate license to us from Splunk software.
The Splunk apps frameworks resides within Splunk web server. It allows us to customized Web UI Which comes along with the products. Splunk apps is developed using web servers. It is more important functionality as well as features of the Splunk software. It doesn’t license us to change anything in Splunk software.